Two-factor authentication (2FA), often also called two-factor authentication, describes a user's proof of identity by means of a combination of two different and, in particular, independent components (factors). Typical examples are bank cards and PINs for ATMs, fingerprints and access codes in buildings, or passphrase and transaction number (TAN) for online banking.
2FA in BlueSpice
The extensions OATHAuth und Webauthn make it possible to implement 2FA in BlueSpice. They have to be configured explicitely after activation.
- OATHAuth enables 2FA via one-time password
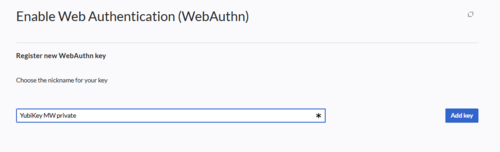
- WebAuthn enables 2FA via FIDO sticks, Windows Hello!, etc.
Activating 2FA (User preferencees)
To activate 2FA for your user account:
- Click Settings in the user menu.
- Click the "Manage" button for Two-factor authentication in the "User profile" tab.
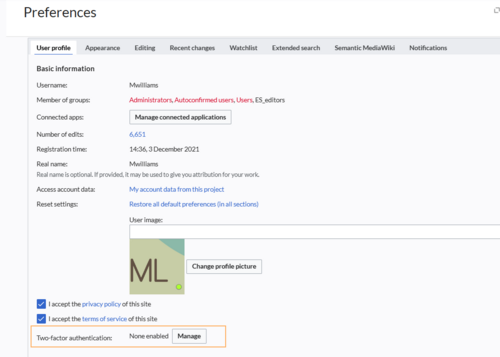
"User profile" tab - Click "Enable" for a method. You will have to confirm your password again. After that, you can select from two options. Follow the respective instructions.
- After setting up your 2FA, log in to the wiki again.
Single-sign on (SSO)
If an external authentication source (SAML, OpenIDConnect und LDAP) is implemented, we recommend to execute 2FA within these sources and not inside the wiki. Compatibility with SAML, OpenIDConnect or LDAP have not yet been tested in BlueSpice.
2FA is not possible with true SSO (LDAP/Kerberos).