|
|
| Line 1: |
Line 1: |
| Here we explain the conceptual basics of BlueSpice software development and explain central procedures with which Hallo Welt! ensures security and reliability in software development.
| | <div class="downloadarea"> |
| | <span class="getButton">[[Media:Startpage Management System.zip|Download]]</span> |
|
| |
|
| == Principles of software development ==
| | [[File:Startpage Management System.png|350x350px]] |
| BlueSpice software development is based on a number of important principles:
| | </div>This template provides a good starting layout for the homepage of the wiki for a small or medium-sized company. |
| | {{Templateimport|1=Startpage Management System}} |
|
| |
|
| * '''Cloud-first approach''': The software is developed for use in our cloud offering and is also regularly released for on-premises installations.
| | {{Messagebox|boxtype=important|Note text=If you want the process map to show, you need to [[#Additional_download|upload it separately]].}} |
| * '''Security-by-default''': All relevant security settings are already activated in the basic configuration of the software and our services.
| |
| * '''Vendor independence through open source development''': Although Hallo Welt! is the sole producer of the BlueSpice software distribution, the code produced by Hallo Welt! is developed with the active participation of the MediaWiki community in the public repositories of the [https://wikimediafoundation.org/ Wikimedia Foundation] and is thus freely accessible. This ensures that support for users of the software can be provided not only by Hallo Welt! but also by other service providers (avoiding a lock-in effect).
| |
| * '''Use of open source standards, technologies and formats''': Hallo Welt! relies on [[wikipedia:Open_standard|open standards]] that are particularly easy to access, extend and use. The necessary server infrastructure can be provided entirely with open source software (e.g. Linux operating systems or MariaDB as database system). The BlueSpice software is based on and uses various open standards (e.g. TLS, TCP/IP, IPv6 as network protocol for communication, as well as HTML, JavaScript, CSS and XML for presentation and function). It uses standardised character sets and encodings and supports the use of open formats such as PNG, Ogg, SVG, CSV or MathML. And of course BlueSpice supports uniform standards for describing metadata such as RDF.
| |
| * '''Secure encryption procedures based on industry standards''': Here, for example, communication between application and user is secured by TLS and passwords are stored securely in the database by hashing. For user authentication, proven standards such as SAML or OpenID Connect can be used.
| |
| * '''Modularity''': The software is modular and object-oriented. Individual functions can be deactivated if necessary and individual requirements can be easily implemented. Compatible extensions from the MediaWiki ecosystem that are not directly part of BlueSpice can also be installed later if required (On Premises).
| |
| * '''Interoperability''': BlueSpice provides various interfaces as well as import and export functions to connect the wiki software with other systems. Tasks can be automated and data exchange between different internal IT systems can be realised via a well-documented web API (including REST). A simple XML-based data format enables the import and export of wiki page content and is suitable, for example, for the migration of existing document inventories. In addition, various authentication systems (Active Directory/LDAP, SAML, Open ID Connect) are available for selection, allowing BlueSpice to be seamlessly integrated into one's own IT infrastructure.
| |
|
| |
|
| == Release policy == | | ==Pages included in the import== |
| New product versions are continuously imported into the cloud systems by Hallo Welt! For on-premises systems, the latest versions are made available for download.
| | The xml import creates the following files in your wiki: |
|
| |
|
| We generally follow this release policy:
| | * Help:Startpage Management System |
| | * Help:Startpage Management System/Banner |
| | * Help:Startpage Management System/Contact |
| | * Help:Startpage Management System/Events |
| | * Help:Startpage Management System/How we document |
| | * Help:Startpage Management System/Iconnav |
| | * Help:Startpage Management System/New pages |
| | * Help:Startpage Management System/Process map |
| | * Help:Startpage Management System/Recent changes |
| | * Template:Bannerbox |
| | * Template:Bannerbox/styles.css |
| | * Template:Dropdown |
| | * Template:Dropdown/styles.css |
| | * Template:Image cards |
| | * Template:Image cards/end |
| | * Template:Image cards/start |
| | * Template:Image cards/styles.css |
| | * Template:Startpage |
| | * Template:Startpage/styles.css |
|
| |
|
| * '''Patch levels''' with bug fixes and security updates are released monthly.
| | == Additional download == |
| * '''Minor levels''' with functional improvements or changes are released once or twice a year.
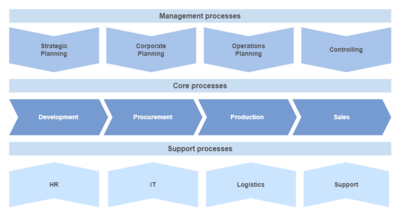
| | [[File:Process map.png|alt=Process map with management, core and supporting processes|thumb|400x400px|Example process map]] |
| * '''Major levels''' are released on average every three years. The release of a major release is indicated,
| | You can upload an example process map to your wiki. |
| ** when features are introduced that greatly change the behaviour of the software,
| |
| ** when new technologies or major upgrades of system components are delivered, or
| |
| ** when changes are made to the system requirements (non-compatibilities).
| |
| * '''Security releases''' or '''security patches''' are published as soon as possible after a security vulnerability becomes known.
| |
|
| |
|
| The release of new versions of BlueSpice follows the version cycle of MediaWiki. '''BlueSpice uses the latest LTS (Long-Term Support) version of MediaWiki'''. This ensures that patches and updates from the MediaWiki community can be continuously applied. In addition, the use of the LTS version is an essential contribution to the stable operation of the various extensions.
| | [https://en.wiki.bluespice.com/w/nsfr_img_auth.php/3/3a/Process_map.png Process map.png] |
|
| |
|
| All changes are published in the [[Setup:Release History|release notes in the BlueSpice Helpdesk]].
| | {{Clear}} |
|
| |
|
| == Continuous documentation == | | == Elements of this start page == |
| Good documentation is essential for the use and further development of a software. The central place for the documentation of the software and its application is the [[Main Page|BlueSpice Helpdesk Wiki]], where you are currently visiting. It is the central contact point for users, administrators and developers. There we provide the following documents centrally and always up-to-date:
| | From top to bottom of the page, you can find the following contents: |
| | | {| class="wikitable" style="width: 100%;" data-ve-attributes="{"style":"width: 100%;"}" |
| * [[Setup:System requirements|System requirements]] for the operation of BlueSpice
| | ! style="width:200px;" data-ve-attributes="{"style":"width:200px;"}" |Section |
| * [[Setup:Installation Guide|Installation instructions]] for the local installation of the software
| | ! Subpage |
| * [[Setup:Software Catalogue|Software catalogue]]: Scope of the current release
| | !Content type |
| * [[Setup:Release History|Release history]]: Description and release notes of the various BlueSpice versions
| | !Description |
| * [[:Category:Extension|References of all extensions]]: Description of function, technical information (e.g. dependencies, configuration options, API modules and hooks).
| | |- |
| * Furthermore, manuals can be found there:
| | | style="width:200px;" data-ve-attributes="{"style":"width:200px;"}" | Banner |
| ** [[Manual:User manual introduction|User manual]]
| | | Banner |
| ** [[Manual:Admin Manual Introduction|Admin manual]]
| | |Template |
| * [[Setup:BlueSpice Operating Manual|BlueSpice operating manual]] with diagrams of the architecture, among other things.
| | |The banner parameters are described on the [[Templates download/Banner|Banner download page]]. |
| | | |- |
| == Quality management and testing ==
| | | Iconnav |
| The use of software in institutions and companies further requires that the machine data processing functions as error-free as possible. Therefore, the following procedures are applied in BlueSpice software development: | | | Iconnav |
| | | |Template |
| * '''Versioning of the source code'''
| | | The icon nav uses FontAwesome icons out of the box. Up to BlueSpice 4.2, those are not included as an extension. In this case they have to be replaced with Bootstrap Icons or an external reference to FontAwesome has to be added to MediaWiki:Common.css (if allowed by the security policies of the company). The parameters are described on the [[Templates download/Image cards|Image cards download page]]. |
| ** All changes to the source code can be traced at any time via appropriate source code management software (GIT SCM).
| | |- |
| ** Additional quality assurance takes place through constant code review procedures (Gerrit, Gitlab-MR, Github-PR), so that potential errors can be detected early and do not even reach the publication stage.
| | |How we document our processes |
| ** It is also ensured that only authorised persons can change the source code.
| | |How we document |
| * '''Automated software tests and scans (static code analysis)'''
| | |Text |
| ** In addition to manual code reviews of upcoming changes, the code is also tested automatically. After each change to the source code, special software tests (unit, integration and E2E tests) ensure that the entirety of the application has not been negatively affected. Tools used to review and test code and application:
| | |You can add any text you like. |
| *** We use a code review tool (Gerrit). This includes tests per commit (unit, security). In addition, we scan the included libraries daily for known vulnerabilities. The tests and scanners are partly provided by the Wikimedia Foundation and meet the requirements of Wikipedia.
| | |- |
| *** UnitTest: PHPUnit, QUnit
| | | style="width:200px;" data-ve-attributes="{"style":"width:200px;"}" |Events |
| *** IntegrationTest: PHPUnit
| | |Events |
| * '''Continuous integration'''
| | |Text |
| ** The software is built automatically every day, installed on test servers and tested. A fault-free run of the tests is a prerequisite for delivery, both in the cloud and for the on premise releases. The tools used for this are:
| | |Simple static table with example events. You can add links to wiki pages or replace the entire table with your own content. |
| *** E2ETest: Selenium
| | |- |
| *** Performance Test: Apache JMeter
| | | style="width:200px;" data-ve-attributes="{"style":"width:200px;"}" |Contact info |
| *** Security scan: Trivy
| | |Contact |
| * '''User acceptance tests'''
| | |Text, Tag:profileimage |
| ** New features and major modifications are pre-tested by an internal test team.
| | |Content can be edited directly on the page. Double-click on the [[Manual:Extension/BlueSpiceAvatars|profile image tag]] to change the user name for the contact avatar. |
| * '''Penetration tests and vulnerability assessments'''
| | |- |
| ** Penetration tests and vulnerability assessments are carried out for BlueSpice in cooperation with strategic customers and partners.
| | | style="width:200px;" data-ve-attributes="{"style":"width:200px;"}" |Process map |
| ** The test results are evaluated and flow into the software development.
| | |Process map |
| ** Third-party test results are not published.
| | |Draw.io, Text |
| | | |The process map uses the draw.io extension (pre-bundled in BlueSpice ''pro'') to show an editable process map. In BlueSpice free, you can simply upload a static image and add it to the page. |
| == Closing security gaps quickly == | | Below the process map is an accessible (barrier-free) text-based list of all processes (replace these with your own static or [[Page lists|dynamic]] process list). |
| Hallo Welt! has taken a number of measures to close security gaps as quickly as possible:
| | |- |
| | | |New pages |
| * '''Vulnerability Disclosure Policy for reporting security issues'''
| | |New pages |
| ** Users can report vulnerabilities and security problems to Hallo Welt! at any time. There is also a [https://bluespice.com/filebase/vulnerability-disclosure-policy/ policy for dealing with security-related errors and problems].
| | |Smartlist |
| * '''Disclosure of security vulnerabilities'''
| | |Uses the the [[Manual:Extension/BlueSpiceSmartList|SmartList tag]] to show the latest 5 pages that were added to the wiki. |
| ** Hallo Welt! notifies all customers who might be affected by the security vulnerability. This is done by informing customers by email and via the [https://bluespice.com/#newsletter BlueSpice newsletter].
| | '''Click''' on the SmartList and '''select''' ''Edit'' to change its options. |
| ** Hallo Welt! is further authorised by the [https://www.cve.org/ CVE programme] ''CVE Numbering Authority'' (CNA). This means that all security vulnerabilities are recorded by BlueSpice in a central, publicly accessible database. Users and automatic security scanners can thus identify vulnerable versions of BlueSpice, assess the severity and receive information on how to fix the problems.
| | |- |
| * '''List of Security Advisories'''
| | |Recent changes |
| ** Security advisories are published on the [[Security:Security Advisories|Security Advisories]] page in the BlueSpice Helpdesk.
| | |Recent changes |
| * '''Security releases''' and '''security patches'''
| | |Smartlist |
| ** In BlueSpice Cloud systems, security patches are applied automatically.
| | |Uses the the [[Manual:Extension/BlueSpiceSmartList|SmartList tag]] to show the latest 5 pages that were edited. |
| ** For on-premises systems Hallo Welt! provides a new version ("security release") or security patches for download and implements these in systems supported by Hallo Welt!
| | '''Click''' on the SmartList and '''select''' ''Edit'' to change its options. |
| | | |} |
| == User authentication, encryption and cryptographic procedures ==
| |
| The protection of data files, messages or transmission channels is a central task for software manufacturers in view of the intensified threat situation due to cyber attacks. BlueSpice supports data protection and information security with appropriate functions. These include standard functions such as an '''authentication procedure''', customisable '''rights management''' or the '''stand-alone capability''' of the software (see also [[Info:Trust and Safety/Privacy and information security|Data protection and information security]]).
| |
| | |
| In addition, the following functions make it much more difficult for an external attack to succeed:
| |
| | |
| * '''Single sign-on protocols (SSO)''' - BlueSpice uses standard procedures for secure authentication:
| |
| ** SAML 2.0 and OAuth 2.0 Bearer Token are fully supported.
| |
| ** Open ID Connect (OIDC) can be supported.
| |
| ** Alternatively, the distributed authentication service Kerberos is also possible.
| |
| * '''Password Policy''' - A password policy is set up in BlueSpice which can be customised. The most important functions and options are:
| |
| ** Passwords are entered covertly.
| |
| ** The minimum length of passwords is configurable (default: 10 characters).
| |
| ** The composition of passwords (upper case letters, lower case letters, numeric characters and symbols) is configurable.
| |
| ** The maximum number of invalid attempts is configurable (default: 5 attempts).
| |
| ** The duration of the lockout period is configurable (default: 5 minutes).
| |
| ** The password change interval (number of days before the system forces the user to change the password) is configurable.
| |
| ** Locking of inactive user IDs is possible (via the UserManager).
| |
| ** Deleting inactive user IDs is possible via a server script.
| |
| | |
| * '''Multi-factor / two-factor authentication (MFA/2FA)''' - In BlueSpice, multi-factor authentication can be activated for end-user identification.
| |
| ** Two methods are offered:
| |
| *** OATHAuth enables 2FA via one-time password (TOTP, Time-based One-time Password Algorithm), e.g. via Google Authenticator.
| |
| *** WebAuthn enables 2FA via FIDO sticks, Windows Hello! etc.
| |
| ** The functions for 2FA / MFA are deactivated when delivered and must be activated.
| |
| ** It should be noted that after activating multi-factor authentication, single sign-on is no longer possible.
| |
| * '''Encryption when transmitting via the public internet and when transferring files or data via networks''':
| |
| ** In BlueSpice Cloud systems, access via HTTPS (with TLS) is standard. Here, the customer can use his own certificate.
| |
| ** When installing on site (On Premises), the customer's infrastructure is used. Here, too, all communication can be configured for secure transmission of files and data.
| |
| * '''Encryption to protect data at standby''' (database, files, backup media) is possible in principle.
| |
| ** The encryption of the on-premise systems must be set up and maintained by the customer or their service provider.
| |
| ** Encryption does not take place in the BlueSpice Cloud.
| |
| | |
| {{Textbox|boxtype=important|header=|text=Please note that BlueSpice free has a reduced range of functions. For example, the extensions for single sign-on and two-factor authentication are not delivered with BlueSpice free.|icon=yes}}
| |
| | |
| == External links ==
| |
| * Verena Hösl: [https://www.youtube.com/watch?v=fPtDYvwhoDE BlueSpice Product Development -from Planning to Documentation], BlueSpice Summit 2022. (German)
| |
| * Open Source Business Alliance: Security: [https://osb-alliance.de/featured/sicherheit-open-source-software-und-proprietaere-software-im-vergleich Open Source Software and Proprietary Software in Comparison], 21 June 2022. (German)
| |
| * Product website:
| |
| ** [https://bluespice.com/products/technology/open-source/ BlueSpice and Open Source]
| |
| ** [https://bluespice.com/buy/faq/ BlueSpice: Frequently asked questions]
| |
| ** [https://bluespice.com/secure-wiki/ Secure Wiki]: Solution for securing wiki pages using crypto procedures.
| |
| | |
| [[de:Info:Trust_and_Safety/Software_-_Sicherheit_und_Zuverlässigkeit]]
| |

Discussions